What You Need to Know About Windows 10 Activation
What is Windows 10 Activation?
Windows 10 activation is a critical step that ensures your system is legally licensed, activated, and eligible for all official updates. While you can activate Windows 10 using an official product key or a Microsoft account, some users prefer using a Windows 10 activator tool as a free alternative to bypass the cost of purchasing a key.
However, using a Windows 10 activator comes with risks, as these tools are not officially supported by Microsoft and may violate the EULA (End User License Agreement).
Methods for Activating Windows 10
Official Microsoft Activation: The Safe and Legal Option
Official activation ensures that your Windows 10 copy is genuine. You will need a valid product key or to sign in with a Microsoft account to activate your system. This method is the most secure and fully supported by Microsoft.
- Advantages:
- 100% legal and secure.
- Access to official updates and support.
- No risks related to malware or viruses.
Using a Windows 10 Activator Tool for Free Activation
For those who cannot afford the official Windows 10 activation process, a Windows 10 activator tool can be used to activate your system for free. Tools like KMSPico and KMS Activator emulate a KMS server to bypass the need for a valid product key.
- How Windows 10 Activator Works:
- Download the Windows 10 activator tool.
- Run the tool to simulate a KMS server on your machine.
- The tool activates Windows 10 by connecting to the emulated server, bypassing the need for a product key.
- Advantages:
- Free activation of Windows 10.
- Quick setup process, usually requiring just a few minutes.
- Risks:
- Violates Microsoft’s EULA and is not legal.
- Potential for malware if downloaded from untrusted sources.
- No official support or updates from Microsoft.

| Feature | Official Microsoft Activation | KMSPico Activation | KMS Activator |
|---|---|---|---|
| Activation Method | Product key or Microsoft account | KMS server emulation | KMS server emulation |
| Legality | 100% Legal | Violates Microsoft’s EULA | Violates Microsoft’s EULA |
| Security | High (official, verified tool) | Low (potential malware risks) | Low (potential malware risks) |
| Activation Speed | Fast (depends on internet connection) | Fast | Fast |
| Support | Full Microsoft support and updates | No support | No support |
| File Type | Official installer | ZIP file (tool) | EXE file (tool) |
| Compatibility | Works on Windows 7, 8, 10, 11 | Works on Windows 7, 8, 10, 11 | Works on Windows 7, 8, 10, 11 |
| Download Source | Microsoft website, authorized resellers | Community forums, trusted blogs | Community forums, trusted blogs |
| Risk of Malware | None (from official sources) | High (if downloaded from untrusted sources) | High (if downloaded from untrusted sources) |
| Reactivation | Once activated, no reactivation required | Every 180 days (automatic renewal) | Every 180 days (automatic renewal) |
Step-by-Step Guide to Using a Windows 10 Activator
Step 1: Choose Your Activation Method
Before activating Windows 10, decide whether you will use the official method or a Windows 10 activator tool. If you want the safest and legal option, it’s better to go with the official activation. However, if you’re using a Windows 10 activator, make sure to understand the risks involved.
Step 2: Download the Tool from a Trusted Source
If you’re using a Windows 10 activator tool, download it from a trusted source. Use websites or forums that are well-known in the community to avoid malware. Always check the file integrity before running the tool.
Step 3: Run the Activation Tool as Administrator
To activate Windows 10 using a Windows 10 activator, right-click the tool and select ‘Run as Administrator’. This step ensures that the tool has the necessary permissions to activate your system.
Step 4: Activate Windows 10
- Open the Windows 10 activator tool.
- Click the ‘Activate’ button to start the process.
- Wait for the activation process to complete.
Step 5: Restart Your Computer
After activation, restart your computer to finalize the changes. This ensures that Windows 10 is fully activated.
Troubleshooting Common Windows 10 Activation Issues
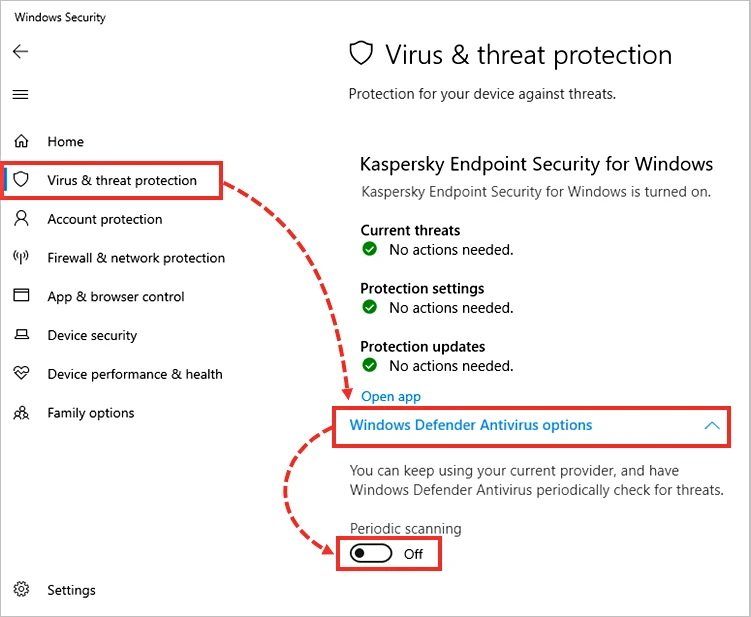
Antivirus Blocking the Windows 10 Activator
If your antivirus software detects the Windows 10 activator as a potential threat, temporarily disable your antivirus during installation. Afterward, add the tool to the exception list in your antivirus software.
“Access Denied” Error
If you see an “Access Denied” error, ensure you’re running the Windows 10 activator as an Administrator and check your User Account Control (UAC) settings.
Legal and Security Risks of Using a Windows 10 Activator
Legal Risks of Using Windows 10 Activators
Using a Windows 10 activator violates the Microsoft EULA, which means it’s illegal to use these tools in many regions. If Microsoft detects the tool, it could result in deactivation of your system or legal consequences.
Security Risks with Unofficial Activation Tools
While a Windows 10 activator may work to activate your system, downloading from untrusted sources can expose your computer to viruses, malware, or data theft. Always download from verified and trusted websites.
Alternatives to Using Windows 10 Activator
Official Microsoft Activation
The best and safest method for activating Windows 10 is through Microsoft’s official activation process. This will guarantee that your system is legally activated, and you will have access to official support and updates.
Volume Activation for Businesses
If you need to activate multiple copies of Windows 10, volume activation is an option for businesses. This method allows organizations to activate Windows 10 on several systems using a single product key.
Frequently Asked Questions (FAQ) About Windows 10 Activation
Can I Activate Windows 10 Without a Product Key?
Yes, you can activate Windows 10 with a Windows 10 activator tool, but be aware that these methods are not legal and come with risks.
Why Does My Windows 10 Keep Saying “Activation Failed”?
If you encounter an activation failure, it could be due to an invalid product key or interference from antivirus software. Follow the troubleshooting steps in the guide to resolve this issue.
How to Check if My Windows 10 is Activated?
You can check the activation status of Windows 10 by going to Settings → Update & Security → Activation. This will show if your system is activated or not.
Let’s Summarize
This guide covers both official and Windows 10 activator methods for activating Windows 10. While official activation is the safest option, activation tools like KMSPico and KMS Activator offer free alternatives but come with legal and security risks. Always weigh the pros and cons before deciding which method to use.